§ Data Agreement (DA) Specification
Specification Status: version 2.1.0 (Released and implemented)
Latest version: Avaialble here
Editors:
- Mr. Jan Linquist (Linaltec, Sweden)
- Ms. Lotta Lundin (iGrant.io, Sweden)
- Mr. Lal Chandran (iGrant.io, Sweden)
Contributors and Reviwers:
- Mr. George Padayatti (iGrant.io, Sweden)
- Dr. David Goodman (iGrant.io, Sweden)
- Mr. Pekka Lampelto (PrivacyAnt, Finland)
Participate:
§ Abstract
A Data Agreement records the conditions for an organization to process personal data in accordance with privacy regulation (e.g. GDPR) captured in a signed receipt given to the individual. To automate creation of the record and increase the trust assurance a Data Protection Impact Assessment may be used to populate the record.
§ Introduction
This specification describes how a Data Agreement between an organisation and individual is managed in order to capture, in a receipt, the conditions of processing of personal data. The receipt acts as evidence and demonstrates a higher level of accountability and is based on standard schemas. The accountability is further enhanced by directly integrating the Data Agreement with the input from a risk assessment, e.g. Data Protection Impact Assessment.
In order to create the Data Agreement, and the resulting receipt as proof, a number of steps are required from different actors. This document describes these steps involved and is described as part of a Data Agreement lifecycle.
§ Abbreviations
| Abbr | Expanded form |
|---|---|
| ADA | Automated Data Agreements |
| CRUD | Create / Read / Update / Delete |
| DA | Data Agreement (Introduced in this specification) |
| DID | Decentralized Identifier (according to W3C) |
| DPIA | Data Protection Impact Assessment |
| DS | Data Source |
| DUS | Data Using Service |
| EEA | European Economic Area |
| EU | European Union |
| GDPR | General Data Protection Regulation |
| ISO | International Organization for Standardization |
| JSON | JavaScript Object Notation |
| SDK | Software Development Kit |
| SSI | Self Sovereign Identity |
| ToIP | Trust over Internet Protocol |
| UC | Use case |
| VC | Verifiable credentials |
| W3C | World wide web consortium |
§ Data Agreement lifecycle actors
These actors are involved in the Data Agreement lifecycle.
- a Data Source, the organisation collecting private data, (typically a data controller). [SSI: Issuer]
- a Data Subject or Individual. [SSI: Holder]
- a Data Using Service (DUS), an organisation processing personal data from one or more data sources to deliver a service. [SSI: Verifier]
- an Assessor reviews the practices of an organisation**, **conducts a DPIA and drafts data agreements and inter-company agreements for third parties.
- an Auditor may be called in to review the data agreements and ensure they are in place in case of data breaches or regular inspection.
In addition to these actors to better understand the interworking, these nodes are relevant.
- Assessment Platform or DPIA Tool is used by Assessor to create reports and populate Data Agreements.
- ADA Service represents the microservices that can be plugged into any service provider wishing to adopt ADA services.
§ Data exchange agreements landscape
This chapter introduces various agreements and relationships that exist between organisations and individuals, depending on their roles in the personal data usage scenarios in a personal data economy. The various agreements involved can be classified into two broad categories:.
- Agreement between an individual and an organisation
- Agreement between two organisations
This specification focuses on agreement between an individual and an organisation; the agreement between two organisations is not within the scope of this specification and is mentioned here for the sake of completion.
§ Agreement between an individual and an organisation
This is an agreement between organisations and individuals in the use of personal data. We refer to this as the “Data Agreement” which can have any of the legal basis that is outlined as per data protection law or regulation, such as the GDPR. The agreement with individuals could be with a Data Source (issuer) or a Data Using Service.
The focus of this specification is on the Data Agreement, how it is defined, prepared by an organisation wishing to use personal data, how it is negotiated with an individual and finally how an auditor is able to audit the data agreement involved in a data transaction.
§ Agreement between two organisations
There can be two forms of agreements between two organisations.
The first form of agreement is between organisations where one organisation acts as a Data Source and the other as Data Using Service. In this case, both organisations share the role as data controller and are responsible for managing their compliance requirements. They may have made their own privacy risk assessment, documented in a data protection impact assessment (DPIA) report, and concluded whether any additional mitigation effort was required. This agreement is referred to as Data Disclosure Agreement, which, though not yet standardised, captures the agreement between two organisations on how data is shared and what obligation each party has. This can be realised as a contract or in terms of use. The individual (data subject) is engaged with both organisations. For each organisation, there exists a Data Agreement with an associated privacy policy that explains the purpose of processing personal data, what personal data is collected, data subject rights, etc.
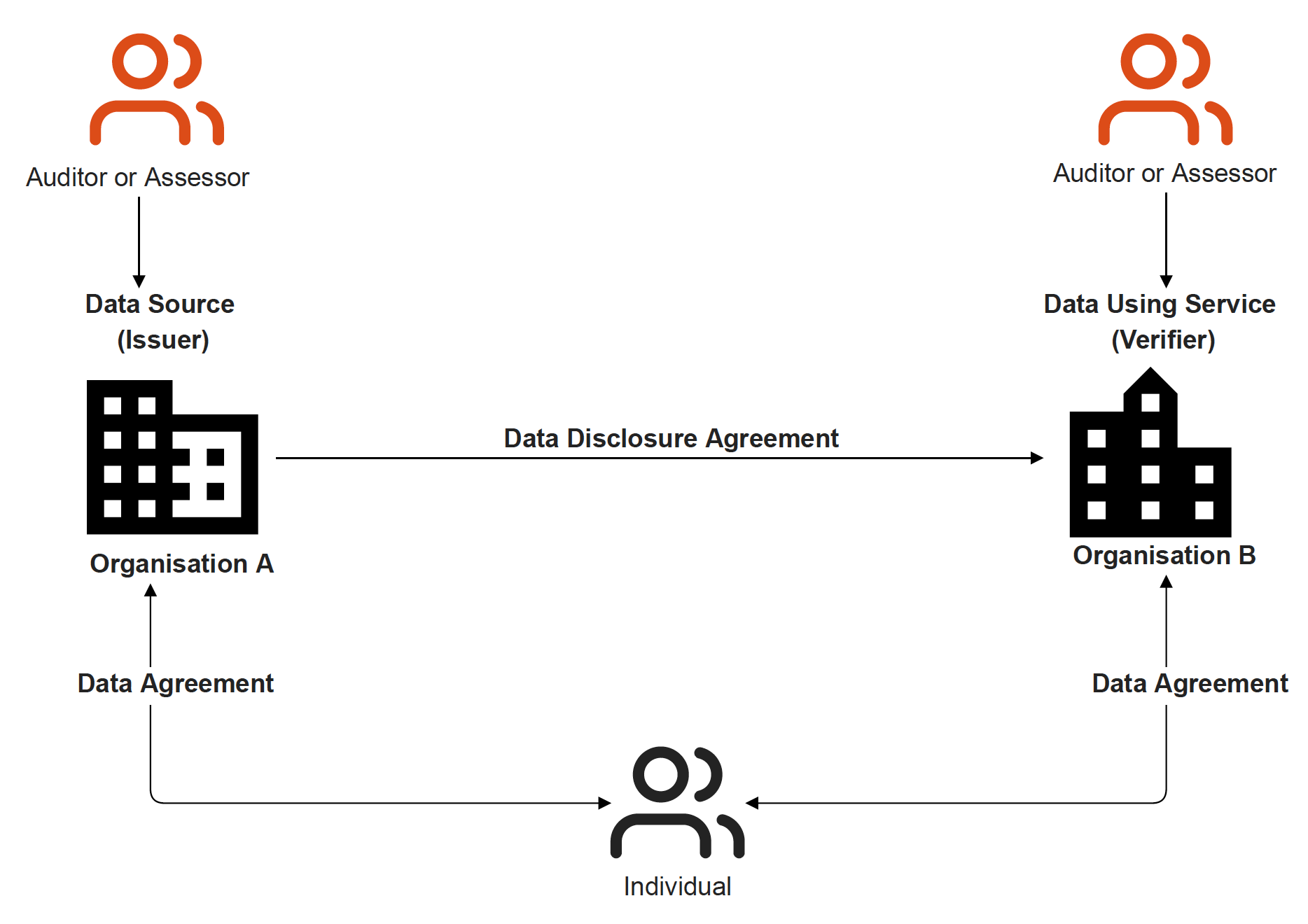
The second form of an agreement in this category is between an organisation and their suppliers as illustrated below.
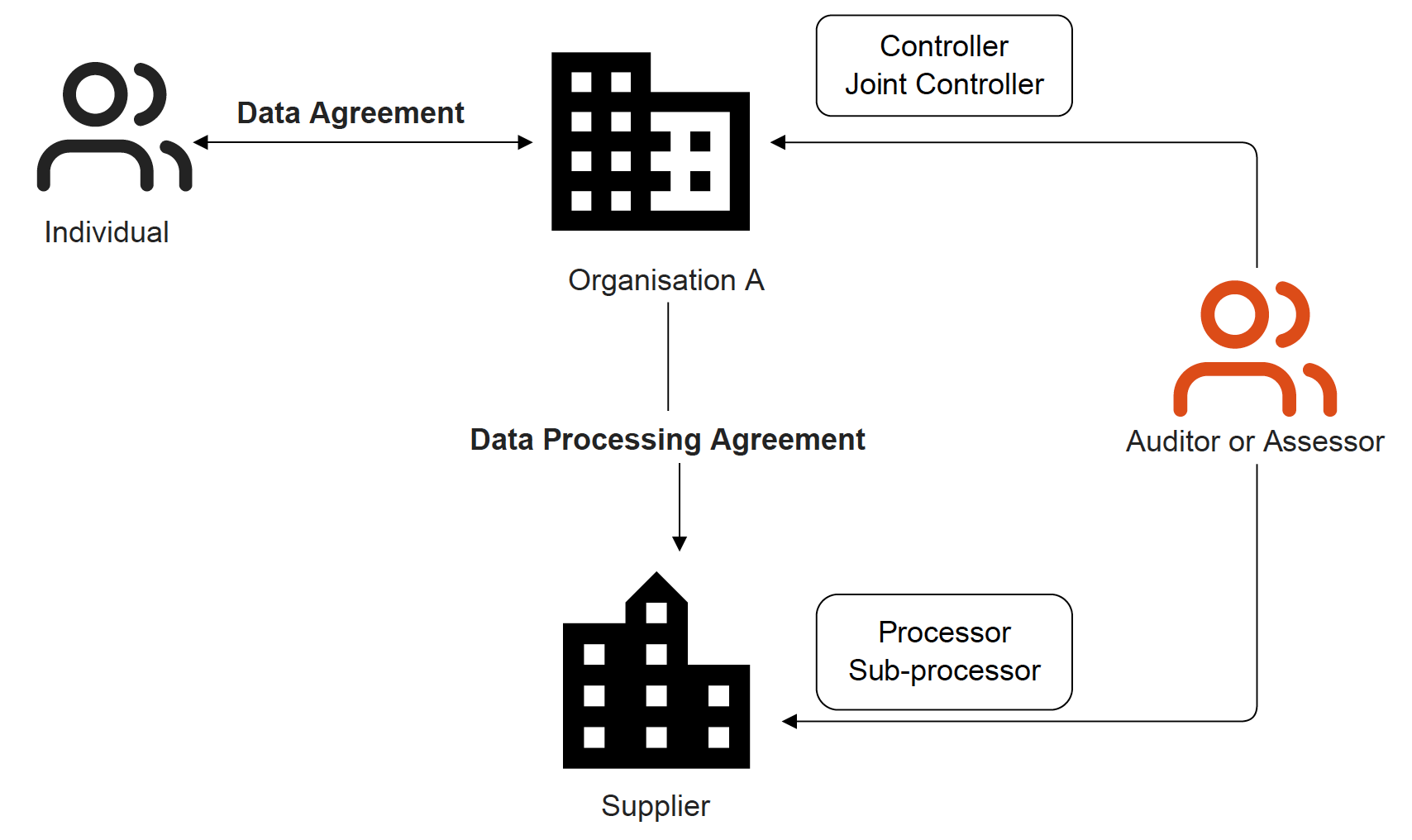
Here, there is a vertical relationship between an organisation A as a data controller and their suppliers as data processors or sub-processors. For a higher level of accountability between these organisations, a Data Processing Agreement is set up, which lays out what routines are required to be in place: for example, data processor’s obligations in case of data breaches or how rights of the data subject, such as access rights, are supported, among other policies and routines. An auditor should also be able to inspect an organisation, and use the data processing agreement as reference during the inspection.
As depicted in the diagram above, the data agreement with the individual is bound to the top of the hierarchy, i.e. the data controller or organisation.
§ Data Protection Impact Assessment (DPIA)
A Data Protection Impact Assessment (DPIA) is a structured process where an organisation can identify and minimise the data protection risks involved in the use of personal data. It ensures that an organisation is compliant to data regulations, such as the GDPR.
Article 35 of the GDPR requires organisations to conduct DPIAs, especially when the processing is likely to result in high risk to the rights and freedoms of natural persons in the case of extensive use of new technologies and when sensitive personal data is being processed (e.g. health-related data). Organisations can also conduct DPIAs voluntarily, even if the processing does not meet the requirement criteria set out in the GDPR.
Some EU Member State data protection authorities, such as the Finnish data protection ombudsman, have recommended using dataflow maps when conducting DPIAs. Dataflow maps visualize the flows of personal data across systems, organisations, and jurisdictions, and provide a good overview of the nature and scope of the processing and identify risks.
Appendix B outlines how a DPIA report can map to a Data Agreement. By integrating the DPIA into the lifecycle of the Data Agreement an organisation can demonstrate how the privacy requirements of accountability, transparency, data sharing and retention procedures are fulfilled. If the DPIA report is part of an online tool it is possible to continuously monitor an organisation’s data flows and ensure any internal changes are reflected in the Data Agreement.
§ Data Agreement functional overview
This section provides a functional overview of the Data Agreement and is broken down into:
- Data Agreement lifecycle
- Applicable use cases
- Overview of how the actors interwork
§ Data Agreement Lifecycle
The Data Agreement Lifecycle has 4 main phases as described below:
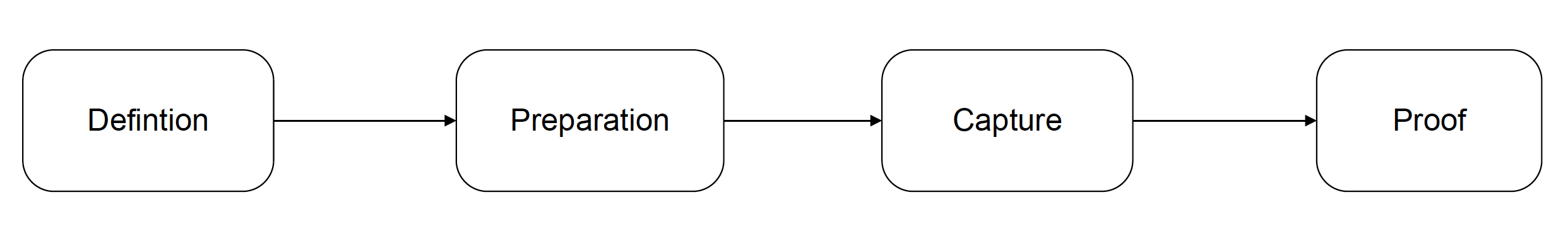
- Definition: In this phase, an authority adapts the data agreement schema to a particular industry and/or sector specific data usage as a template. This can then be used by any organisation (Data source or Data Using Service) for a particular data usage purpose.
- Preparation: In this phase, an organisation uses an existing data usage template and prepares it to be published towards the individuals. This could be based on a DPIA and could be for internal use of data or for data exchange to a Data Using Service. Once the Data Agreement is prepared,any changes identified from a subsequent DPIA shall update the Data Agreement and go through a new preparation process. When an agreement is updated or terminated, the individuals are notified and a record is created.
- Negotiation/Capture: In this phase, an individual reviews the Data Agreement and, once agreed, it is captured in a Data Agreement record by the organisation and the individual is given a Data Agreement receipt as evidence of the agreement. The Data Agreement receipt can be used as proof for the data transaction that occurred. This allows an auditor to check and ensure records are in place to process the individual’s personal data. When the agreement is terminated and is no longer applicable towards an individual, a new record is created. The termination can be due to the service period being completed or an individual requests to revoke the agreement. The record of the termination allows an auditor to inspect personal data that is not used. If an individual requests to be forgotten when terminating a service it shall be clearly indicated.
- Proof: An organisation is able to demonstrate a valid Data Agreement record for performing a data exchange with an individual. This allows an auditor to check and ensure records are in place to process the individual’s personal data.
How each actor is involved in the different phases can be found in this table.
| Actors | Definition | Preparation | Capture | Proof |
| ADA Service | X | X | X | X |
| Individual or Data Subject | X | X | ||
| Data Source or Data Using Service | X | X | X | X |
| Assessor or a DPIA tool | X | X | ||
| Auditor | X |
§ Use Cases
These are the use cases covered by this specification. A mapping between the use cases and lifecycle phase can help map to the involved actors described in the previous section.
| # | Lifecycle Phase | Use Case |
| 1 | Definition | Create template Data Agreement for both human and machine readable formats |
| 2 | Update Data Agreement based on changes on assessment (DPIA) | |
| 3 | Preparation | Prepare Data Agreement based on an assessment (DPIA) |
| 4 | Update Data Agreement based on changes on assessment (DPIA) | |
| 5 | Capture | Countersign a Data Agreement and capture Data Agreement receipt in negotiation/capture phase |
| 6 | Data agreement revoked/expired | |
| 7 | Proof | External audit of Data Agreement |
§ Sequence diagrams
§ Definition and Preparation phases
“Definition” and “Preparation” phases of the Data Agreements lifecycle have the following functions which can be seen in the sequence diagram.
-
Populate the Data Agreement. This could be based on a DPIA or a self evaluation. This calls the CRUD (Create/Read/Update/Delete) operations on the Data Agreement(s).
-
Publish/unpublish Data Agreement(s) towards deployments by ADA Service. When it is published, it’s available towards the individual.
§ Negotiation/Capture phase
In this phase, an Individual can Sign and Revoke (Opt-out) a data agreement which results in a data agreement receipt. The signing can be performed using a unique identifier during the creation of a verifiable credential or when performing proof presentation for example when showing proof of identity. Typically the proof may be expected to be the first step to connect with an organization.
§ Issuing credentials (Data Source)
The below sequence diagram shows how the steps of issuing a credential can be used to present and agree on the Data Agreement. The Data Agreement will be presented as an offer and once accepted a receipt is created. The sequence of actions are:
- A Data Source offers to issue data and adds a reference to a signed Data Agreement.
- Once the user agrees to the data offer and accepts it, the agreement is counter signed and a receipt is created.
The following diagram is from Aries 0036 Issue Credential and the text in red represents how a Data Agreement is processed as part of a credentia offer when it is accepted or rejected.

§ Verifying credential (Data Using Service)
The below sequence diagram shows the Data Agreement flows for a verifier or Data Using Service, when requesting data to be shared by the individual. The sequence of actions are:
- A Data Using Service makes a request for proof and adds a reference to a signed Data Agreement.
- Once the user agrees to the data offer and accepts it, the agreement is counter signed and a receipt is created.
The following diagram is taken from Aries 0037 Presentation Proof and the text in red represents how the Data Agreement is processed in the offer and accepted with the option to reject.

§ Termination
The Data Agreement may be terminated in a number of ways. Here are a few of the scenarios:
- Data Agreement expired and the service is no longer applicable
- Updated Data Agreement with new purpose or changes to collected pii categories
- Individual requests to terminate the service before expiration date
- Individual requests not only terminate but have their personal data erased
Note the erasure may come after termination of the Data Agreement.
The following diagram is the case for individual requests to terminate scenario 3, individual requests termination.
§ Proof
In accordance with GDPR Art. 30, Records of processing activities, a Data Controller (Data Source and DUS) shall record processing activities under its responsibilities. The records shall be available to the individual to inspect in the form of a receipt and provide means of an audit. An audit can be initiated due to the following reasons:
- Complaint by Data Subject (Or Individual)
- Review of Data Source or Data Using Service record logs
The complaint by Data Subject (Or Individual) will include a copy of the Data Agreement receipt and explanation of the violation by Data Source or DUS.
The following sequence is the approach taken when the auditor reviews implementation of Data Agreement capture and withdrawal. If the auditor lacks the software to perform the read then a dashboard access is provided by the Data Source or DUS. In case of a Data Subject complaint, a reference to the original Data Agreement is shared with the Auditor so the Auditor can perform the same verification.
§ References
[1] Data Agreement Interface Specification
[2] Data Agreement - DID Method Specification
[3] Kantara Consent Receipt Specification
[4] ISO/IEC 29184: 2020: Information Technology - Online Privacy Notices and Consent (Published, available at https://www.iso.org/standard/70331.html)
[5] ISO/IEC TS 27560 — Privacy technologies — Consent record information structure (Not published yet)
§ Appendix A: Data Agreement schema
This section describes the content of the Data Agreement. The schema is based on Kantara Consent Notice [3], as well as ongoing ISO standardization under ISO project 27560, Consent record information structure. Note ISO/IEC TS 27560 [5] is not yet published as it is only referred to by field names but the input requirements for 27560 is the published ISO standards 29184, Information technology - Online privacy notice and consent [4].
Table below captures, at a high level, the various attributes to be collected when recording and creating Data Agreement receipts. This is based on analysis of the DPIA reporting and the various standards analysed.
|
|
|
|
|
|
|
|
NOTE: For deeper analysis of the DPIA mapping exercise refer to this link.
The following table lists the required fields in the Data Agreement. The attribute names are from ISO 27560 and for better insight the Kantara 1.1 fields are included.
| Data element identifier | Kantara 1.1 fields | Description | Required |
| Record metadata | |||
| schema_version | version | An identifier for the implementation documentation to which the record conforms. | Required |
| consent_record_id | consentReceiptID | A unique number for each consent record. | Required |
| PII processing | |||
| notice_timestamp | consentTimestamp | Date and time that the consent was obtained.
The number of seconds since 1970-01-01 00:00:00 UTC. |
Required |
| privacy_notice_URL | policyURL | A link to the PII controller’s privacy notice and applicable terms of use in effect when the consent was obtained, and the receipt was issued. If a privacy policy changes, the link SHOULD continue to point to the old policy until there is evidence of an updated consent from the PII principal. | Required |
| language | language | Language of notice and interface related to consent. | Required |
| purposes | purposes | An implicit or explicit reference to an array that contains one or more items where each item represents one Purpose. | Required |
| purpose_category | purposeCategory | A broad category providing further description and context to the specified purpose for PII processing. | Optional |
| pii_categories | piiCategory | An explicit list of PII categories to be processed for the specified purpose. The categories shall be defined using language meaningful to the users and consistent with the purposes of processing. The PII categories may be represented implicitly, across all consent records of this type in the consent record handling system | Required |
| services | services | An implicit or explicit reference to an array that contains one or more items where each item represents one Service. | Required |
| service | service | A service or group of services being provided for which PII is collected, represented by the name of the service for which consent for the collection, use, and disclosure of PII is being provided. | Required |
| pii_controllers | piiControllers | An array that contains one or more party_identifier values where each identifier represents one PII controller. A corresponding party identification structure shall exist in the party identification section for each array element | Required |
| collection_method | collectionMethod | Clear explanations of the PII collection methods being used, along with information about any risks associated with particular PII collection methods. | Required |
| method_of_use | How the PII will be used
If the PII principal was informed of the processing operations employed by the PII controller(s) to process the PII, under the auspices of this consent, then that information may be recorded as part of the consent record. |
Required | |
| jurisdiction | jurisdiction | The geo-location(s) where PII will be stored and processed, and the legal jurisdiction(s) that govern the handling of the data. | Required |
| third_party_name | thirdPartyName | The name or names of the third party to which the PII processor may disclose the PII. | Required |
| withdrawal | Indicates information or link on how/where the PII principal can withdraw this consent. | Required | |
| code_of_conduct | The PII controller may follow a code of conduct which sets the proper application of privacy regulation taking into account specific features within a sector. The code of conduct shall reference the name of the code of conduct and with a public accessible reference. | Optional | |
| assessment | The PII controller may perform a privacy assessment in order to determine privacy risks and potential impacts to non-compliance of the PII principals. The assessment instance is a reference to the latest assessment and shall include assessment name (e.g. PIA or DPIA), when assessment was signed off and reference to the assessment firm. If certification is provided for the assessment it shall be included. | Optional | |
| sensitive_pii_categories | spiCat | A PII controller may explicitly note some PII categories that are considered sensitive where this has an impact on the consent or its use for the specified purpose or in other contexts such as the sharing with other parties. | Optional |
| Party identification | |||
| party_id | An unambiguous identifier indicating the party within the record. | Mandatory | |
| party_postal | address | Contact information in the form of postal address | Optional |
| party_email | Contact information in the form of email address | Optional | |
| party_url | piiControllerURL | Contact information in the form of web site address | Optional |
| party_phone | phone | Contact information in the form of phone number | Optional |
| Consent section contents | |||
| consent_timestamp | Date and time that the consent was obtained.
The number of seconds since 1970-01-01 00:00:00 UTC. |
Required | |
| consent_duration | The period from the date and time when the consent was given to the date and time of its termination. | Optional | |
| pii_principal_id | piiPrincipalId | An identifier provided by or associated with the Principal. E.g., email address, claim, defined/namespace or pseudonymized identifier. | Required |
| consent_type | consentType | The PII controller shall indicate the consents type used to disclose privacy notice with the PII principal. | Required |
| termination | termination | Indicates that the consent referred to in the record has been terminated by the specified condition or event. Termination of consent indicates its unsuitability to be used as continued basis for the processing of PII. | Optional |
| retention | The amount of time a pii data is kept after which they are removed. | Optional (new) | |
| expiration | How long a consent is valid for before expiring | Optional (new) | |
§ Appendix B: DPIA (Risk Assessment)
This appendix describes how a DPIA reports maps to the Data Agreement. For deeper analysis of the DPIA mapping exercise refer to this link. DPIA reports are typically composed of the following sections:
- Overview
- Scope
- Roles and responsibilities
- Processing Overview
- Scope of Processing
- Context of Processing
- Stakeholder Engagement (Data Subject)
- Compliance with data protection law and other regulatory guidance
- Identify and Assess Risks
- Identify measures to Reduce Risks
- Sign off and Record Outcomes
The key areas for input to the Data Agreement are Roles and Responsibilities, Scope of Processing and Context of Processing. The Context of Processing establishes the lawful basis for processing personal data. The Roles and Responsibilities lists all involved entities like data controllers, data processors and sub-processors.
The Scope of Processing section looks into private data processing in more detail. Typically this sections covers the following:
- Data Subject Categories
- Data Types
- Data Collected/Processed
- Data Retention
- Parties Access/Use (member/role/access)
- Personal Data (attribute level, type, collection activity, frequency)
§ Data Agreement mapping from DPIA
The following table provides a mapping between the DPIA report and the Data Agreement.
| Data Agreement | DPIA |
| Purpose(s) | |
| Purpose - describe (highest risk first) | 8. Compliance with data protection law and other regulatory guidance
+ 9. Identify measures to Reduce Risks |
| pii categories related to purpose (what is collected) | 5.6. Personal Data (attribute level, type, collection activity, frequency) |
| Service name applicable for purpose | 2. Scope |
| Processing | |
| Collection method (directly, indirectly, observed, inferred, etc.) | 4. Processing Overview |
| Method of use (as is, after processing, combined, automated decision making) | 4. Processing Overview
+ 5.3 Data Collected/Processed |
| Retention (how long data kept) | 5.4. Data Retention |
| Jurisdiction data stored | 7. Compliance with data protection law and other regulatory guidance |
Transfer to which third parties
|
5.5. Parties Access/Use (member/role/access) |
| Optional: Assessment performed | 10. Sign off and Record Outcomes |
| List of sensitive pii categories | 5.6. Personal Data (attribute level, type, collection activity, frequency) |
§
§ Appendix C: Standards Input
This section serves as a reference to some of the material that has been used for the development of the Data Agreement schema.
§ Kantara Schema Reference
Kantara Consent Receipt Specification v1.1.0
| Attribute | Type | Required | Description |
| version | string | REQUIRED | |
| jurisdiction | string | REQUIRED | REQUIRED: The jurisdiction(s) applicable to this transaction. This field MUST contain a non-empty string describing the jurisdiction(s). |
| consentTimeStamp | integer | REQUIRED | REQUIRED: Date and time of the consent transaction. The JSON value MUST be expressed as the number of seconds since 1970-01-01 00:00:00 GMT. ISO 8601 Date and Time Format [ISO 8601] MUST be used for formatting. |
| collectionMethod | string | REQUIRED | REQUIRED: A description of the method by which consent was obtained. Collection Method is a key field for context and determining what fields MUST be used for the Consent Receipt. This field MUST contain a non-empty string. |
| consentReceiptID | string | REQUIRED | REQUIRED: A unique number for each Consent Receipt. SHOULD use UUID-4 [RFC 4122]. This field MUST contain a non-empty string. |
| publicKey | string | OPTIONAL | |
| language | string | OPTIONAL | |
| piiPrincipalId | string | REQUIRED | REQUIRED: PII Principal-provided identifier. E.g., email address, claim, defined/namespace. Consent is not possible without an identifier. This field MUST contain a non-empty string. |
| piiControllers | array | REQUIRED | REQUIRED: Name of the first PII Controller who collects the data. This entity is accountable for compliance with the management of PII. The PII Controller determines the purpose(s) and type(s) of PII processing. There may be more than one PII Controller for the same set(s) of operations performed on the PII, in which case the different PII Controllers SHOULD be listed. For Sensitive PII, the PII Controller MUST be specified with legally required explicit notice to the PII Principal. This field MUST contain a non-empty string. |
item |
|||
| policyUrl | string | REQUIRED | REQUIRED: A link to the PII Controller’s privacy statement/policy and applicable terms of use in effect when the consent was obtained, and the receipt was issued. If a privacy policy changes, the link SHOULD continue to point to the old policy until there is evidence of an updated consent from the PII Principal. This field MUST contain a non-empty string. |
| services | array | REQUIRED | REQUIRED: An array that contains one or more items where each item represents one Service. It is only required for the JSON encoding of a Consent Receipt. |
| purpose | string | OPTIONAL | OPTIONAL: A short, clear explanation of why the PII is required. |
| consentType | string | REQUIRED | REQUIRED: A description of the method by which consent was obtained. Collection Method is a key field for context and determining what fields MUST be used for the Consent Receipt. This field MUST contain a non-empty string. |
| purposeCategory | array | REQUIRED | REQUIRED: The reason the PII Controller is collecting the PII. Example Purpose Categories currently in use are available on the Kantara Consent & Information Sharing Work Group (CISWG) Wiki page (https://kantarainitiative.org/confluence/x/74K-BQ). This field MUST contain a non-empty string. |
| piiCategory | string | REQUIRED | REQUIRED: A list of defined PII categories. PII Category should reflect the category that will be shared as understood by the PII Principal. More information can be found on the Kantara Consent & Information Sharing Work Group (CISWG) Wiki page. (https://kantarainitiative.org/confluence/x/74K-BQ). This field MUST contain a non-empty string. |
| primaryPurpose | boolean | OPTIONAL | OPTIONAL: Indicates if a purpose is part of the core service of the PII Controller. Possible values are TRUE or FALSE. |
| termination | string | REQUIRED | REQUIRED: Conditions for the termination of consent. Link to policy defining how consent or purpose is terminated. This field MUST contain a non-empty string. |
| thirdPartyDisclosure | boolean | REQUIRED | REQUIRED: Indicates if the PII Controller is disclosing PII to a third party. Possible values are TRUE or FALSE. |
| sensitivity | boolean | REQUIRED | REQUIRED: Indicates whether the consent interaction contains PII that is designated sensitive or not sensitive. Possible values are TRUE or FALSE. A value of TRUE indicates that data covered by the Consent Receipt is sensitive, or could be interpreted as sensitive, which indicates that there is policy information out-of-band of the Consent Receipt. |
| spiCat | array | REQUIRED | REQUIRED: A listing of categories where PII data collected is sensitive. The field MUST contain a non-empty string if Sensitive PII is TRUE. |
§ ISO Standards
The two ISO standards relevant to Data Agreements are as below.
-
ISO/IEC 29184: 2020: Information Technology - Online Privacy Notices and Consent
-
ISO/IEC TS 27560 — Privacy technologies — Consent record information structure
